Blog
Insights into today’s security and compliance challenges
Articles
Reactive Security the Pros and Cons
Why it’s hard to stop Reactive Security Many find themselves in a cycle of reactive security. They are responsible for security but are part of small to mid-sized enterprises (SMEs). This situation means there is usually no formal 24/7 security operations...
Growing Cyber Insurance Concerns
Many small to medium-sized enterprises (SMEs), if they have not yet experienced the changes in cyber insurance, are in for a surprise. Whether you seek insurance for the first time or are renewing an existing policy, there will be changes. Cyber insurance concerns are...
CISA Exploited Vulnerability Catalog Increases by 21%
‘That escalated quickly’ comes to mind when looking at the 95 new exploited vulnerabilities CISA added on March 3rd, then an additional 12 on March 7th. With these two additions, the known exploited vulnerability catalog increased by 21%. This represents a...
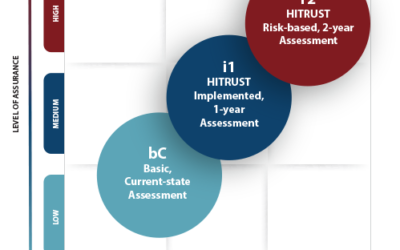
New HITRUST Assessment Options for Business Associates
HITRUST has rolled out several changes providing new assessment options for organizations to achieve various levels of assurance. Overall, there are three assessments, each helping organizations to evaluate and understand the effectiveness of their cyber preparedness...
Cybersecurity Talent Crisis Will Forever Change IT
Even before the ‘great resignation’ companies were struggling to find, and keep cybersecurity talent. Read about some strategies and solutions for addressing the persistent cybersecurity talent shortage.
What are the Benefits of Penetration Testing?
The Gift of Penetration Testing Penetration testing is one of the best security investments a business can make. In-house IT or security lacks the objectivity to uncover and thoroughly test for the flaws that expose them to potential data breaches. Having an external...